nday dev CVE-2024-5522
After analyzing the plugin and understanding how it works and how it differs, I see some interesting things in this file:
wp-content/plugins/html5-video-player/inc/Rest/VideoController.php
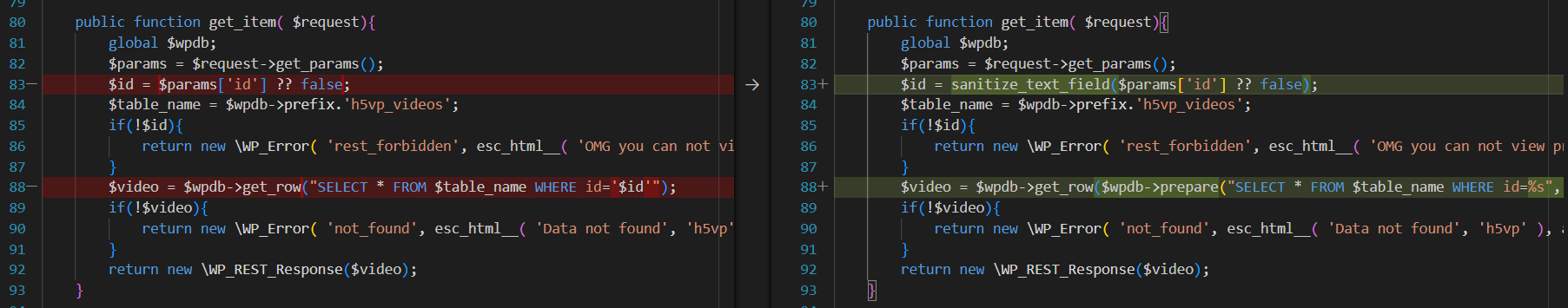
So in this function we can see that the attacker can escape in the sql str and does not need to do anything like add ecape chars or bypass anything
and here we can see the vulnerable route /wp-json/h5vp/v1/video/
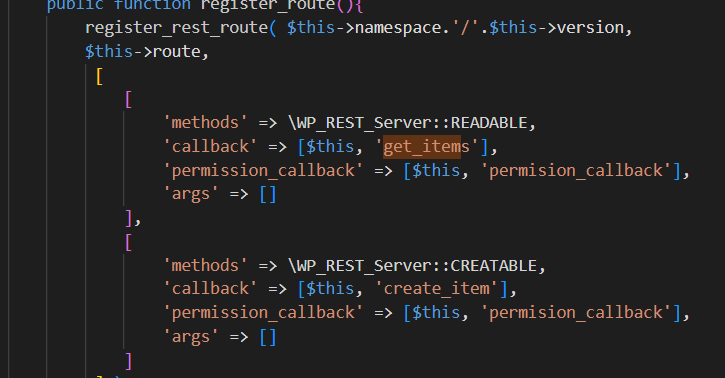
so we know anything we need to know :) also the request method is post and the vulnerable parameter is “id”
request is these:
$request = array( 'method' => 'POST', 'body' => $params, 'timeout' => 60, );
also i see some xss patches in these plugin in the version 2.5.26 of these plugin