pfc 200 exploitation for fun and profit
to day i explain how we can exploit the command injection vulnerability in wago pfc200 firmware.
the command injection is vulnerability to allow attacker to output its own commands at the device and access to it.
vulnerability is on these directory: pfc200/var/www/wbm/php
and filename is :session_lifetime.inc.php
these function sent request is responsible for checking the username parameter in the ID session each time PHPSESS .
we cant injecting the command on the session just we need the check these function where be use on the web server and inject our own command for fun :)
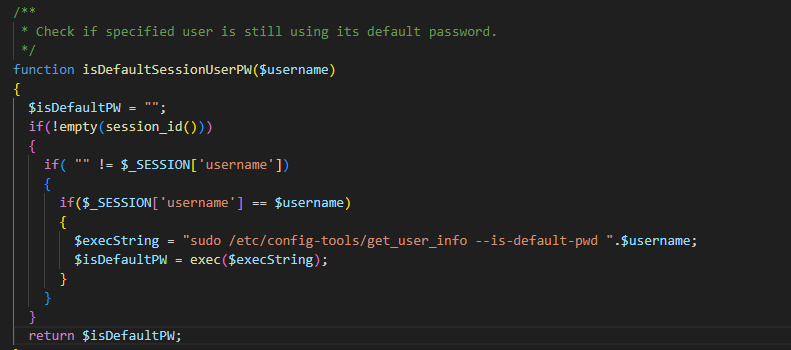
In order to give them a little more time, I will not publish this yet (i talk about poc and other stuff like that)
so these is realy shity command injection on these function :/
why you use these ?
I have reported it but still no response after 1 week also i have 2 other vulnerability on the iocheckd service but i dont like to report it
these is wan side vulnerability and these device is use realy critical infrastructure